By Ajay Kapur
New Delhi. 24 July 2020. Civil Aviation has evolved drastically over the last decades with the evolving advancements in the technology landscape and regulatory reforms resulting in better resilience and growth opportunities in the aviation sector business & its operating models. Along with the benefit of the technologies, cyber threats arise, affecting all systems and IT infrastructures thus impacting highly business continuity of operations as worldwide systems are interconnected. Thus to stay ahead in today’s world, it becomes a necessity for the business or body corporate to ensure early stage cyber threat detection, mitigation, developing incident response strategies and its related legal remediation to mitigate any liabilities arising from any threat vector.
Enhanced interoperability capabilities, usage of IoT for operations (like baggage handling, passenger check in, landside operation controls, common use passenger services and traveller web services) & intelligent applications adopted by smart airports to achieve effectiveness in their operations, has also been increased technical complexities and associated cyber threats. Although many airports have robust systems in place to address common cyber threats, but considering the holistic approach to the cyber environment which includes coverage to all the internal and external threat vectors are critical to mitigate the risks associated with cyber security.
Threats & vulnerability to airport’s cyber security applies to broad categories of assets (which majorly includes communication networks/ VoIP systems, servers and access control systems, internal/sensitive information and authentication etc.) affecting the information security triad CIA (Confidentiality-Integrity-Availability) based on their importance for business operations. Some assets have critical confidentiality requirement (like company trade secrets), some may have critical integrity requirement (based on financial transaction values), and some have critical availability requirements (like e-commerce web servers and communication systems).
According to ENISA (The European Union Agency for Network and Information Security), smart airports are those who make use of networked, data driven response capabilities that, on the one hand, provide travellers with a better travel experience and on the other hand, aim to guarantee higher levels of security for the safety of passengers, operators and general public.
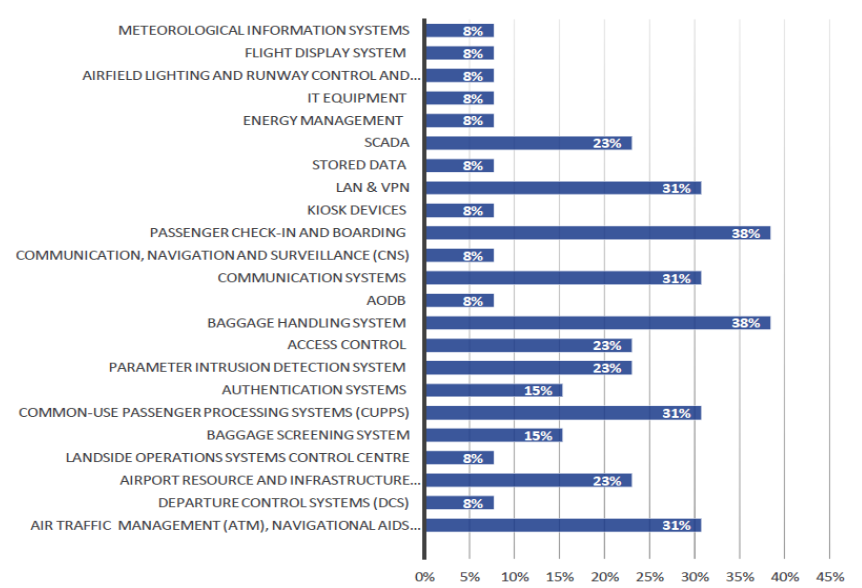
“This table can give an overview of the most critical assets for the 20 organisations across eight countries that provided feedback for the present report.- Courtesy: ENISA”
Although many security threats may occur either by intentional or unintentional factors, leading security incidents related to breach of confidentiality, integrity, availability of organization asset.
Major cybersecurity threats vectors against smart airports can be segregated into the following categories: (i) Network and communication attacks; (ii) Malicious software; (iii) Tampering with Airport Smart Devices; (iv) Misuse of Authorization; and (v) Social and Phishing attacks . The intent of these threat vectors are to:-
- Disrupting computer operations
- Stealing sensitive information, including personal, business, and financial data
- Gaining unauthorized access
- Spying
- Engaging in distributed-denial-of-service attacks (DDOS)
- Locking up the files on the computer and holding them for ransom
Malicious Software Attack:- Use Case
“Malware, or malicious software, infiltrates and gains control over the targeted system or a mobile device without the consent of system owners to steal sensitive information, spy on the infected system, or take control of the system.”
“Malware is any software intentionally designed to cause damage to a computer, server, client, or computer network. A wide variety of types of malware exist, including computer viruses, worms, Trojan horses, ransomware, spyware, adware, rogue software, and scareware.”
Similar attacks can be accomplished with malware installation by attacker to the airport’s website or intranet, where airport users’ devices may be infected, thus giving the opportunity to malicious attackers to access airport’s network and critical information system through these infected devices.
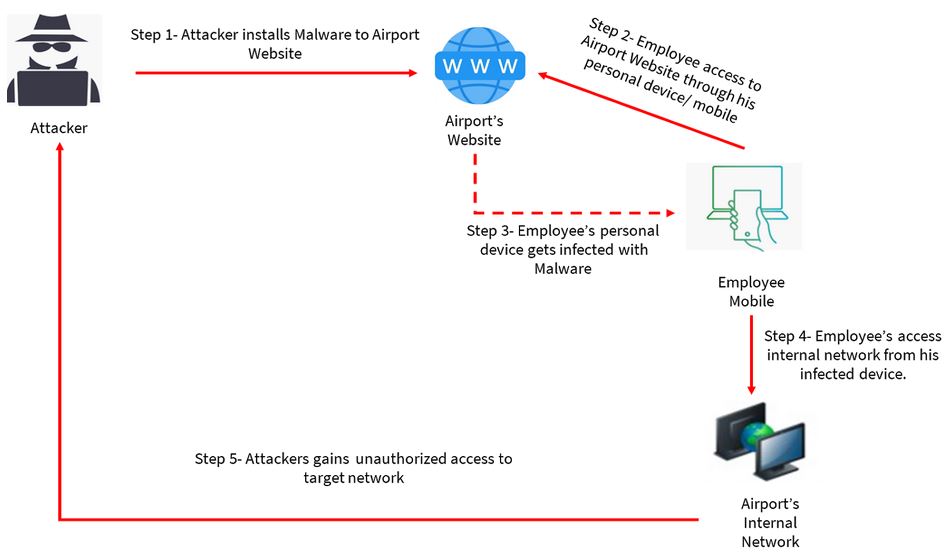
Impact evaluation: Smart airports systems are interconnected to increase their interoperability, so potential attacks can cause network outage, flight cancellations, passenger delays, loss of confidence, major financial damages, where as manipulation of data from essential functionalities and safety parameters like air navigation & air traffic control management systems, communications, aircraft collision avoidance systems and other aircraft management systems which may lead to fatal accident and loss of human lives.
Resilience Measures: Countermeasures includes antimalware and Intrusion Detection & Protection Systems (IDS/IPS) should be implemented. It is important all the software patches and hardware updates to be done on time, so as smart airport’s systems to be kept up-to-date, with reduced exposure to common vulnerabilities. Moreover, the monitoring and audit of systems and log files are also crucial for the resilience of smart airports, because any unauthorized changes by malicious insiders should be immediately detected and remediated. It is said that “what you can’t prevent, you should be able to detect, and if you detect something, it means you weren’t able to prevent it” so preventive, detective, and corrective controls should work together for resilient system.
Regulatory Measure: ICAO
The International Civil Aviation Organization (ICAO) creates regulations for aviation safety, security, efficiency and regularity and environmental protection. Where It was urged to Member States and ICAO in Assembly Resolution A40-10 for Addressing Cybersecurity in Civil Aviation while promoting the universal adoption and implementation of the Convention on the Suppression of Unlawful Acts relating to International Civil Aviation (Beijing Convention) and Protocol Supplementary to the Convention for the Suppression of Unlawful Seizure of Aircraft (Beijing Protocol) as a means for dealing with cyberattacks against civil aviation.
ICAO Resolution A40-10 for Addressing Cybersecurity in Civil Aviation superseded Resolution A39-19, with the focus to develop an action plan and implement Cybersecurity Strategy as the core component for civil aviation industry and to ensure that cybersecurity matters are considered and coordinated in a manner through the appropriate mechanisms in the spirit of the Strategy.
Legal Analysis
Cyber crime is a “combination of crime and computer” while specific to installing malware which caused or tend to cause the destruction to system resources is categorized as computer-targeted crime, where any computer resource is the victim of an attack crafted to harm it (and its owner) specifically, following provisions are mentioned considering the cyber crime as global concern.
In the U.S., United States Code, Title 18 defines the federal crimes, court systems, and punishments of the United States. It has been amended many times to include computer-related crime. The Federal Computer Abuse Act (18 U.S.C. Sec. 1030) outlaws the deliberate “transmission of a program, information, code, or command and as a result of such conduct intentionally causes damage without authorization to a protected computer” (18 U.S.C. Sec 1030(a)(5)(A).
The first prosecution in united states under the Federal computer crime statute , 18 USC § 1030, was for a release of a worm. Robert Tappan Morris, then a graduate student in computer science at Cornell University, released his worm into the Internet on 2 Nov 1988. The worm rapidly copied itself and effectively shut down the Internet. Morris was convicted of violating 18 USC §1030 in 1990 and the conviction was upheld in U.S. v. Morris, Citation 928 F.2d 504 (2dCir. 1991), cert. denied, 502 U.S. 817 (1991).
As per New York Penal laws those who are accused of the distribution of malicious software can be charged with: Code Section 156.05 which states that a person is guilty of unauthorized use of a computer when he or she knowingly uses, causes to be used, or accesses a computer, computer service, or computer network without authorization.
Unauthorized use of a computer is a class A misdemeanor.
India Perspective
The main enactment in India that deals with protection of data is IT ( Information Technology ) Act and the Information Technology (Reasonable Security Practices and Procedures and Sensitive Personal information) Rules, 2011 (the “IT Rules”). India enacted Information Technology Act, 2000, which came into force on 17 October 2000. Amendments in the Information Technology Act, 2000, were carried out and new act was termed as IT (Amendment) Act, 2008 with more Focus on data privacy and Cyber Crimes.
Scope of Section 43 of IT Act – This section mainly deals with accessing the computer, its network or system without permission of the owner. Purpose could be copying, downloading of content, damaging the computer or data or contaminating the data or system using the virus or any other kind or malware also attracts this section. Breach of this section attracts only penalty for the damages which is basically civil adjudication. But if intention of the accused is proved to be fraudulent or dishonest, then the Section 66 of IT Act which states that- “If any person, dishonestly or fraudulently, does any act referred to in section 43, he shall be punishable with imprisonment for a term which may extend to three years or with fine which may extend to five lakh rupees or with both”.
Where as scope of Section 43(A) of IT Act details the provision related to compensation for failure to protect the data and negligence in implementing reasonable practices by body corporate to process, deal and handle any sensitive data or information.
Section 425 of the IPC deals with mischief and provision states that “whoever with intent to cause, or knowing that he is likely to cause, wrongful loss or damage to the public or to any person, causes the destruction of any property, or any such change in any property or in the situation thereof as destroys or diminishes its value or utility, or affects it injuriously, commits mischief”. Damaging computer systems and even denying access to a computer system by mean of hacking or introducing malware will fall within the aforesaid section 425 of the IPC. The maximum punishment for mischief as per section 426 of the IPC is imprisonment of up to 3 (three) months or a fine or both.
The offence under Section 425 of the IPC to be read holistically with Sections 43 and 66 of the IT Act in case introducing and spreading viruses through computer networks, damaging computers or computer networks or computer programmes, disrupting any computer or computer system or computer network etc. Usually filling of complaints under IT Act instinctively inserts provisions of IPC which would require thorough deliberation, so that this would not amount to violation of double jeopardy principle which states that person cannot be tried twice for the same crime based on the same conduct.
Civil aviation sector has key importance for the global and national economies. It contributes to the development of many other sectors. Thus, the role international and domestic aviation security regulators has become more critical to address its growing scale. Although there are continuous endeavours made to harmonize aviation security legislation based on sectoral requirements, where as more effective enforcement mechanisms to be implemented with the goal of increased cooperation within different sectoral entities. On the one hand, the process of technological developments which are becoming more sophisticated, leading to human right and privacy related concerns which requires strategy and control measures with focus on sectoral growth objectives in a broader context.
(The content of this article is intended to provide general information to subject matter only and should be not considered as legal advice. Appropriate advise should be sought based on specific circumstances.)